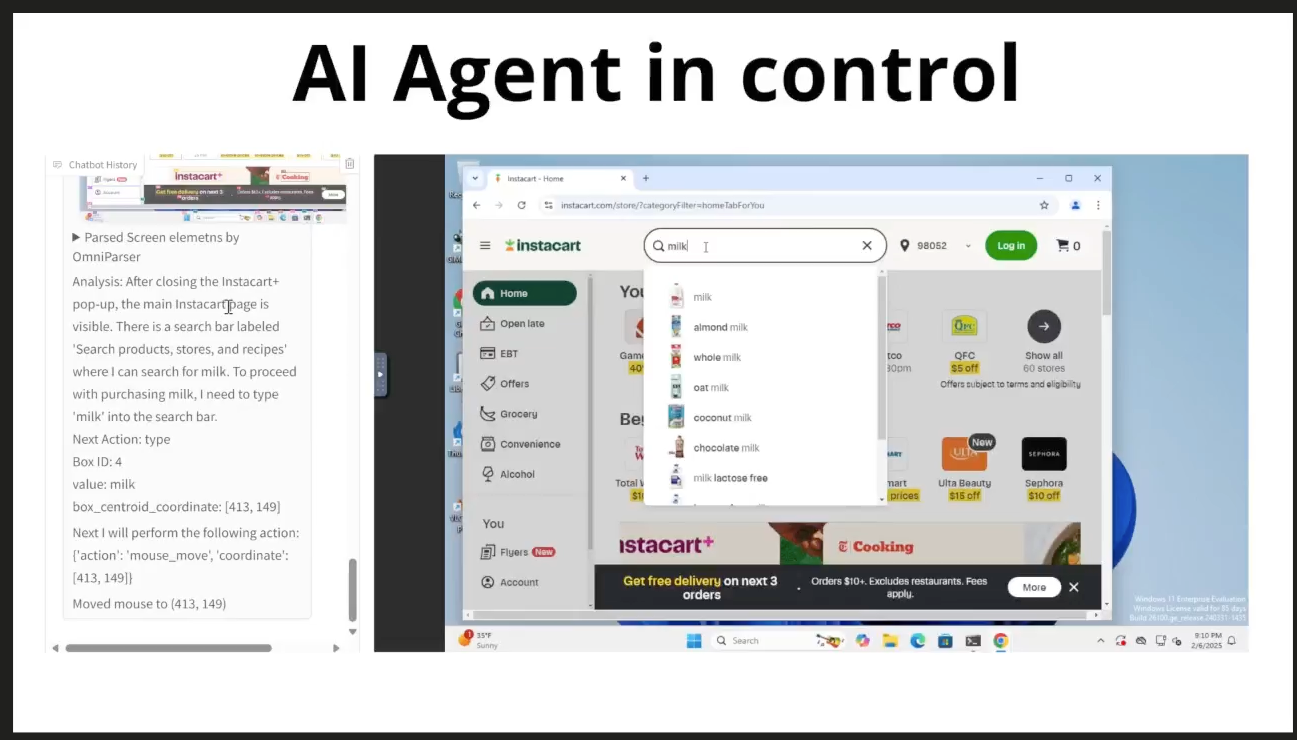
CVE-2025-66479: Anthropic's Silent Fix and the CVE That Claude Code Never Got
allowedDomains: [], “Empty array = no network access.” — Anthropic Sandbox Runtime Documentation The implementation did not match the documentation. When I configured Claude Code’s sandbox with allowedDomains: [], expecting complete network isolation, the sandbox was wide open and allowed connections to any server on the internet. Anthropic patched this quietly in Claude Code v2.0.55 with a changelog entry saying “Fix proxy DNS resolution” — no mention of a critical security flaw. They assigned CVE-2025-66479 to their runtime library but did not assign a CVE to their flagship product Claude Code. The changelog did not include a security advisory. In practice, the issue was fixed quietly and most users were unlikely to realize there was a security patch. ...