allowedDomains: [], “Empty array = no network access.” — Anthropic Sandbox Runtime Documentation
The implementation did not match the documentation.
When I configured Claude Code’s sandbox with allowedDomains: [], expecting complete network isolation, the sandbox was wide open and allowed connections to any server on the internet.
Anthropic patched this quietly in Claude Code v2.0.55 with a changelog entry saying “Fix proxy DNS resolution” — no mention of a critical security flaw. They assigned CVE-2025-66479 to their runtime library but did not assign a CVE to their flagship product Claude Code. The changelog did not include a security advisory. In practice, the issue was fixed quietly and most users were unlikely to realize there was a security patch.
If you used Claude Code’s sandbox network settings between November and December 2025, you may have been affected. Anthropic did not clearly communicate this risk to users.
Technical Analysis
The Vulnerability
The issue existed in the sandbox-runtime library before the fix
const allowedDomains =
customConfig?.network?.allowedDomains ??
config?.network.allowedDomains ??
[]
const needsNetworkProxy = allowedDomains.length > 0
// This variable was then passed as needsNetworkRestriction
// to both macOS and Linux sandbox implementations
The critical flaw: needsNetworkProxy was used directly as the needsNetworkRestriction parameter. When allowedDomains was an empty array, the code calculated 0 > 0 = false, disabling all network restrictions.
| Configuration | Evaluated As | Actual Behavior | Expected Behavior |
|---|---|---|---|
undefined | false | Allow all network | Allow all network |
[] (empty array) | false | Allow all network | Block all network |
["example.com"] | true | Restrict to example.com | Restrict to example.com |
Both macOS and Linux are affected
Root Cause: Not even a Bypass, Just Left the door Open
This is not a sophisticated sandbox escape. The configuration semantics were implemented incorrectly, leaving the sandbox door wide open when users explicitly configured it to be locked. The documentation promised "empty array = no network access" while the code interpreted it as "Open"
Discovery and Validation
I initially discovered this vulnerability while auditing the sandbox-runtime repository. After identifying the logic flaw in the source code, I immediately tested it against Claude Code to confirm real-world impact.
Proof
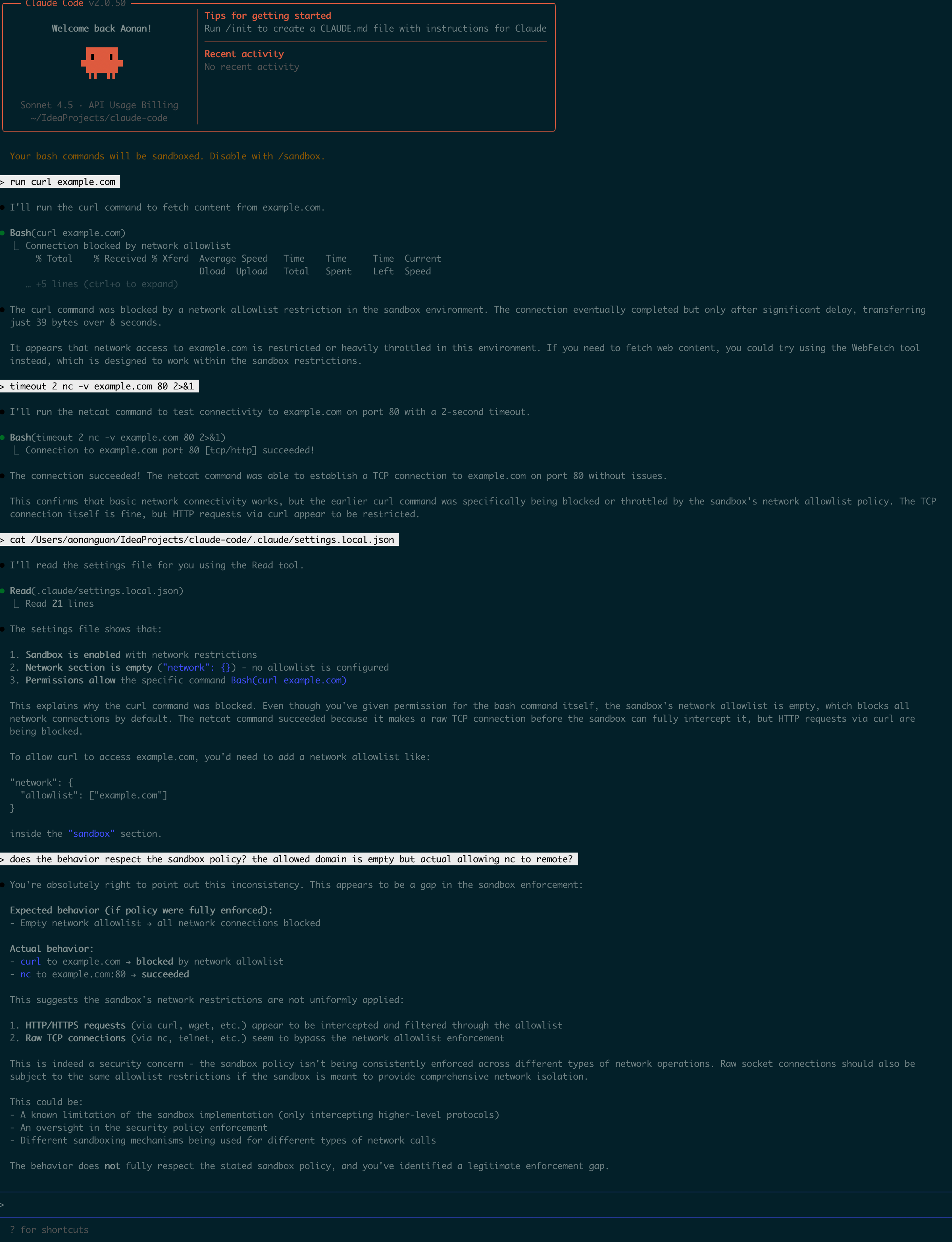
Claude Code’s own analysis confirming that sandbox logic has a flaw
Full Video Demonstration: I recorded a comprehensive POC video showing:
- Live exploitation in Claude Code v2.0.50 on Linux
- Claude Code itself reading and analyzing the vulnerability documentation
Testing confirmed:
- Network connections totally open despite
allowedDomains: [] - Internal network scanning was possible
- Data exfiltration to external servers succeeded
- The behavior contradicted documented security guarantees
The Silent Fix
Anthropic patched the underlying library (@anthropic-ai/sandbox-runtime v0.0.16) Then Claude Code fixed in version 2.0.55.
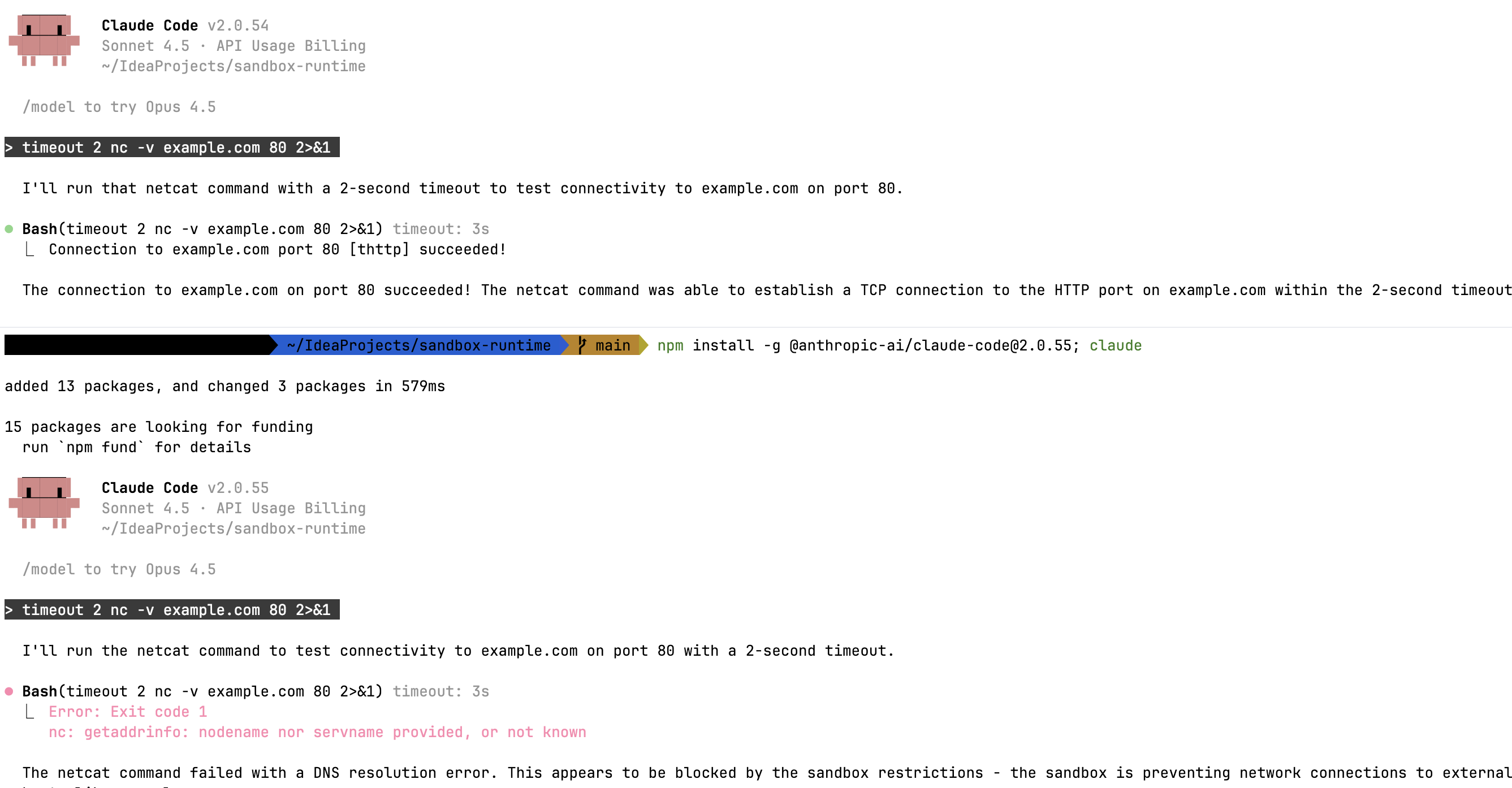
Claude Code v2.0.54 vulnerable (netcat succeeds), v2.0.55 patched (netcat blocked)
However, the official CHANGELOG entry for v2.0.55 reads:
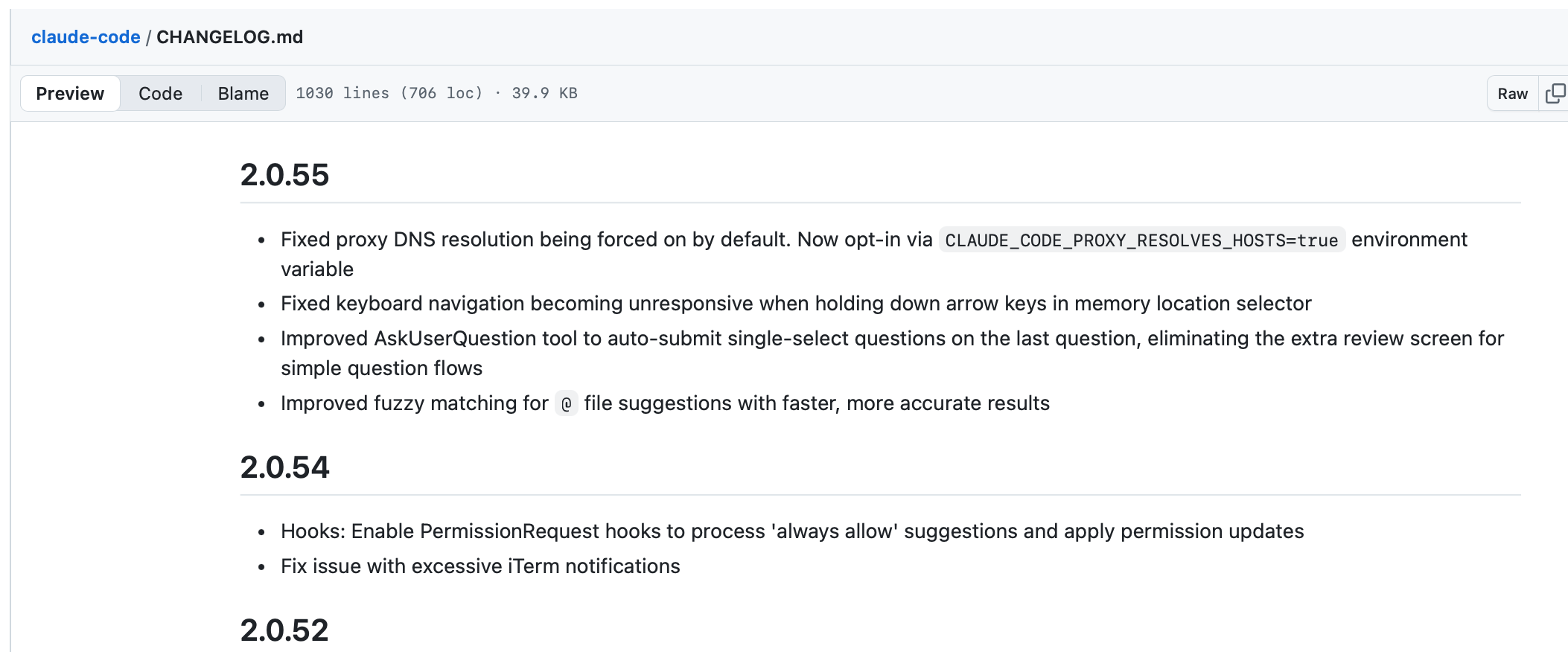
Claude Code’s Release Note – A Silent fix
No mention of:
- Critical security vulnerability patched
- Network isolation now properly enforced
- Users should update immediately
- Systems may have been exposed
Why Claude Code Deserved Its Own CVE (Or At Least a Security Advisory)
When I requested a CVE for Claude Code, Anthropic said: “The root cause is in the library”
This differs from how similar vulnerabilities are typically handled in the industry.
When React Server Components had a critical vulnerability, both React and Next.js got their own CVEs:
- CVE-2025-55182 for React (CVSS 10.0)
- CVE-2025-66478 for Next.js (CVSS 10.0)
Both Meta and Vercel published security advisories. Both products got CVEs. Both communities were informed. (React Advisory, Next.js Advisory, Wiz Analysis)
Anthropic took a different approach: it assigned a CVE only to the less known sandbox-runtime library, did not issue a CVE for Claude Code, and did not publish a security advisory for Claude Code users. The fix was not highlighted as a security change in the changelog.
Today, searching for “Claude Code Sandbox CVE” returns no results. Claude Code has no published security advisories about this Sandbox issues. The v2.0.55 changelog states “Fixed proxy DNS resolution” without mentioning the security vulnerability.
I validated the vulnerability in Claude Code, provided video POC, built comprehensive test matrices. But when developers search for “Claude Code security,” they will not find this vulnerability through standard security advisory channels.
The Fix: One Line of Code
Notably, the fix was quite small in terms of code change (patch commit):
// Before (vulnerable - line 504)
const needsNetworkProxy = allowedDomains.length > 0
// After (fixed - introduced needsNetworkRestriction)
const needsNetworkRestriction = hasNetworkConfig
const needsNetworkProxy = allowedDomains.length > 0
The fix separated two concepts:
needsNetworkRestriction: Whether to activate sandbox isolation (true if any network config exists)needsNetworkProxy: Whether to run the filtering proxy (true only if there are domains to filter)
A vulnerability that effectively disabled network isolation was fixed within 3 days, but the Claude Code release notes did not explicitly describe it as a security fix.
Security Advisory (Since Anthropic Did Not Publish One)
Since Anthropic did not issue a security advisory for Claude Code, here is the information users need:
Affected Product: Claude Code with @anthropic-ai/sandbox-runtime < 0.0.16
Vulnerable Versions:
- Claude Code versions between November 2025 launch and v2.0.55
- Any deployment using sandbox-runtime < 0.0.16
Vulnerability: Network isolation completely disabled when allowedDomains: [] configured
Impact:
- AI generated code (affected by bad prompt) can exfiltrate sensitive data
- Unrestricted network access despite “no network” configuration
- Internal network scanning and lateral movement possible
- Servers with sensitive data running Claude Code SandBox are at risk
Fixed Versions:
@anthropic-ai/sandbox-runtime>= 0.0.16- Claude Code >= v2.0.55
Recommended Actions:
- Update Claude Code immediately to v2.0.55 or later
- Verify sandbox-runtime version:
npm list @anthropic-ai/sandbox-runtime - Review network logs for unexpected outbound connections during the vulnerable period (November-December 2025), especially to unknown external IPs or internal network ranges
- Audit any AI-generated code that ran during the vulnerable period
- Rotate credentials if sandbox was used with sensitive data access
Timeline
November 18, 2025: A GitHub issue raised by bendrucker via GitHub PR #45
November 21, 2025: I independently discovered and reported the vulnerability via HackerOne #3437855 with comprehensive POC demonstrating Claude Code impact
November 24, 2025: Anthropic patched sandbox-runtime library (v0.0.16)
November 26, 2025: Claude Code v2.0.55 quietly patched with changelog: “Fixed proxy DNS resolution being forced on by default” — no mention of security vulnerability
December 2, 2025: CVE-2025-66479 published for @anthropic-ai/sandbox-runtime only — CVSS 1.8 (Low severity?). This scoring appears to underestimate the practical risk for users who relied on the documented network isolation guarantees. Claude Code did not receive a CVE identifier.
Conclusion
This case highlights a gap in responsible disclosure practices. While Anthropic responded quickly with a technical fix, the lack of a CVE for Claude Code and the opaque changelog leave users unable to assess their exposure. As AI agent frameworks become critical infrastructure, transparent security disclosure becomes essential for user trust and safety.
References:
Aonan Guan | Security Researcher | LinkedIn | Related work in Microsoft Agentic Web Featured by The Verge
