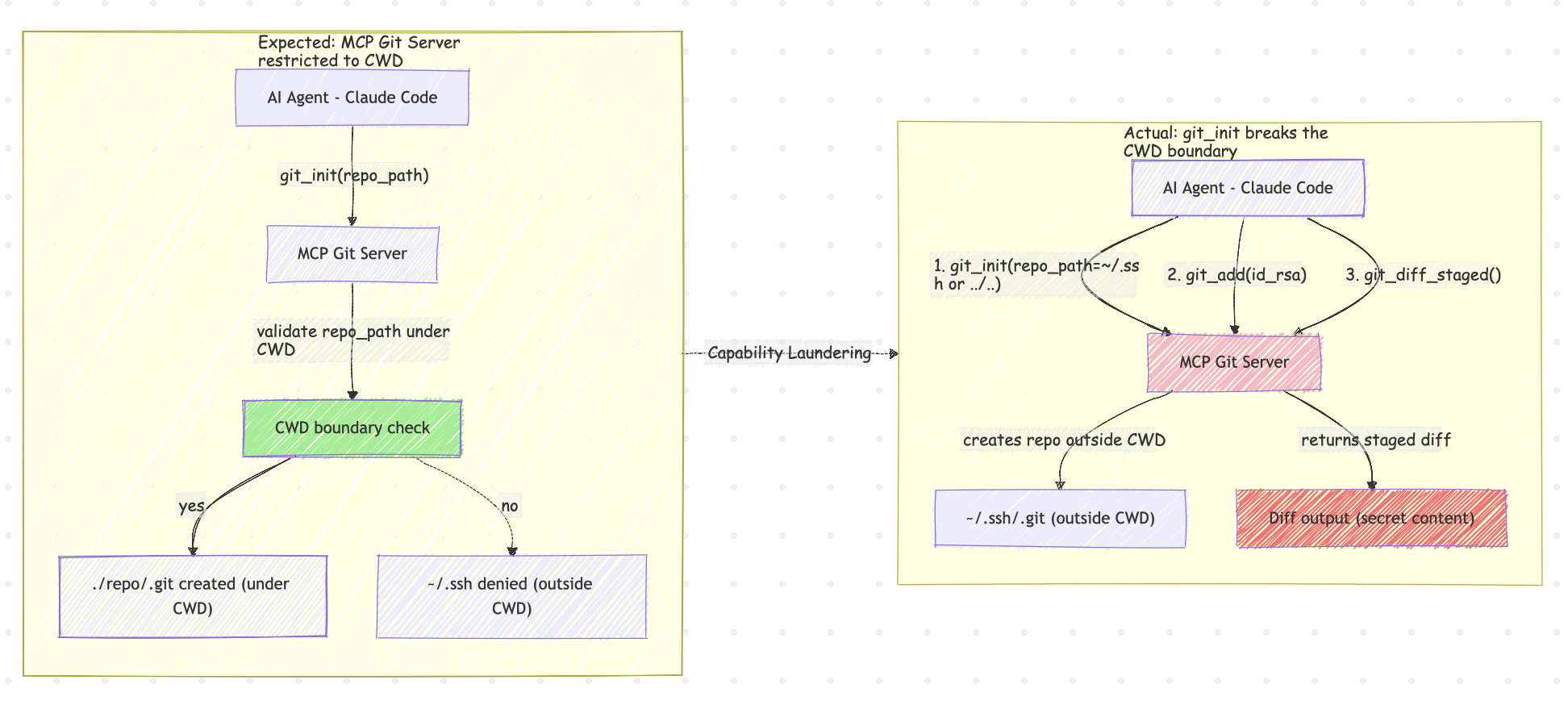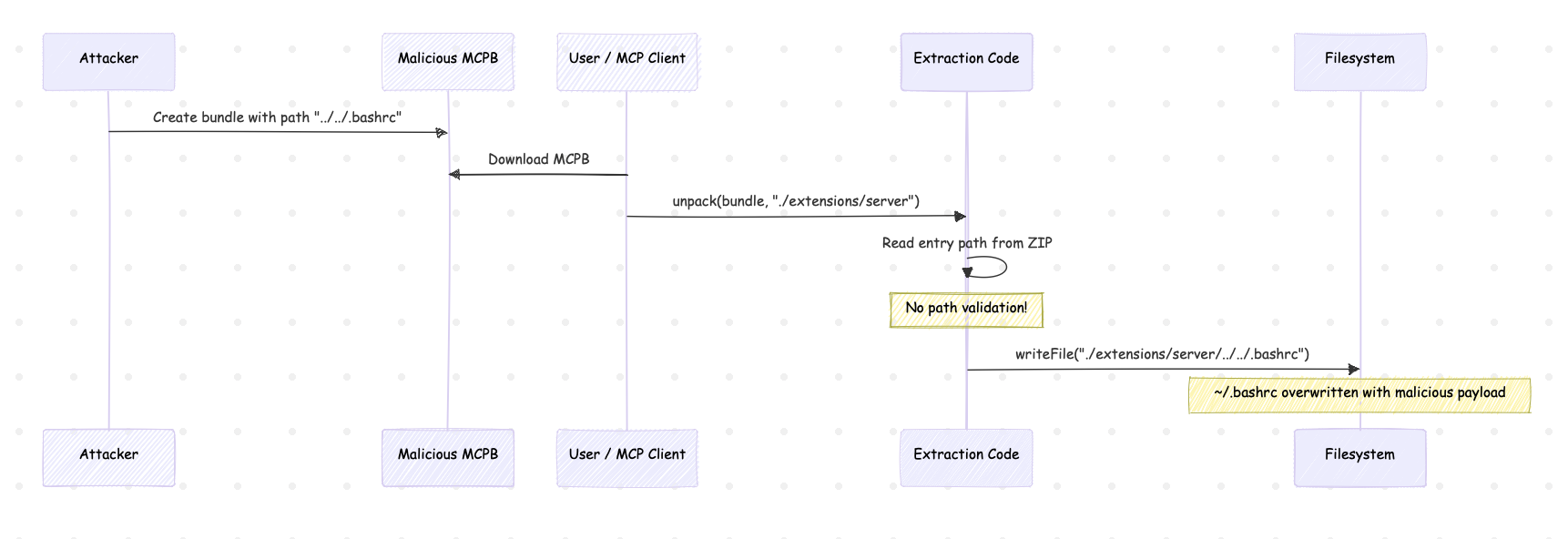
MCP Bundle Security: Zip Slip and Silent Overwrite Risks for MCPB Developers
TL;DR MCPB files are ZIP archives with a .mcpb extension ZIP format has inherent security risks: path traversal (zip slip), silent overwrite, symlink attacks MCPB CLI had zip slip vulnerability before v0.2.6 (fixed in PR #74), still no overwrite warning Adopters using raw libraries like fflate must implement protections themselves What is MCPB? MCPB (MCP Bundles) is the packaging format for distributing MCP servers. Originally developed by Anthropic as “Desktop Extensions,” it was transferred to the Model Context Protocol project in November 2025 (see Adopting the MCP Bundle format (.mcpb) for portable local servers). ...